Microsoft on Tuesday issued an emergency software update to quash a security bug that’s been dubbed “PrintNightmare,” a critical vulnerability in all supported versions of Windows that is actively being exploited. The fix comes a week ahead of Microsoft’s normal monthly Patch Tuesday release, and follows the publishing of exploit code showing would-be attackers how to leverage the flaw to break into Windows computers.

At issue is CVE-2021-34527, which involves a flaw in the Windows Print Spooler service that could be exploited by attackers to run code of their choice on a target’s system. Microsoft says it has already detected active exploitation of the vulnerability.
Satnam Narang, staff research engineer at Tenable, said Microsoft’s patch warrants urgent attention because of the vulnerability’s ubiquity across organizations and the prospect that attackers could exploit this flaw in order to take over a Windows domain controller.
“We expect it will only be a matter of time before it is more broadly incorporated into attacker toolkits,” Narang said. “PrintNightmare will remain a valuable exploit for cybercriminals as long as there are unpatched systems out there, and as we know, unpatched vulnerabilities have a long shelf life for attackers.”
In a blog post, Microsoft’s Security Response Center said it was delayed in developing fixes for the vulnerability in Windows Server 2016, Windows 10 version 1607, and Windows Server 2012. The fix also apparently includes a new feature that allows Windows administrators to implement stronger restrictions on the installation of printer software.
“Prior to installing the July 6, 2021, and newer Windows Updates containing protections for CVE-2021-34527, the printer operators’ security group could install both signed and unsigned printer drivers on a printer server,” reads Microsoft’s support advisory. “After installing such updates, delegated admin groups like printer operators can only install signed printer drivers. Administrator credentials will be required to install unsigned printer drivers on a printer server going forward.”
Windows 10 users can check for the patch by opening Windows Update. Chances are, it will show what’s pictured in the screenshot below — that KB5004945 is available for download and install. A reboot will be required after installation.
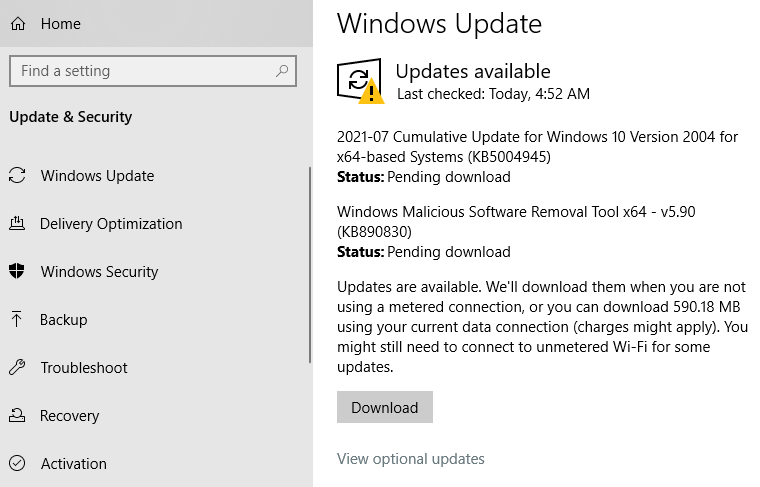
Friendly reminder: It’s always a good idea to backup your data before applying security updates. Windows 10 has some built-in tools to help you do that, either on a per-file/folder basis or by making a complete and bootable copy of your hard drive all at once.
Microsoft’s out-of-band update may not completely fix the PrinterNightmare vulnerability. Security researcher Benjamin Delpy posted on Twitter that the exploit still works on a fully patched Windows server if the server also has Point & Print enabled — a Windows feature that automatically downloads and installs available printer drivers.
Delpy said it’s common for organizations to enable Point & Print using group policies because it allows users to install printer updates without getting approval first from IT.
This post will be updated if Windows users start reporting any issues in applying the patch.
"emergency" - Google News
July 08, 2021 at 06:54AM
https://ift.tt/3hIWmbF
Microsoft Issues Emergency Patch for Windows Flaw – Krebs on Security - Krebs on Security
"emergency" - Google News
https://ift.tt/2VVGGYQ
https://ift.tt/3d7MC6X
emergency
Bagikan Berita Ini














0 Response to "Microsoft Issues Emergency Patch for Windows Flaw – Krebs on Security - Krebs on Security"
Post a Comment